Azure Application Insights - capture client IP
- Roman Guoussev-Donskoi

- Sep 15, 2019
- 1 min read
Updated: May 11, 2023
Microsoft takes a great care to help manage and protect personal data that can be collected in Azure Log Analytics.
For example Azure Application Insights by default obfuscates all IP address fields to "0.0.0.0". (for details please refer to Guidance for personal data stored in Log Analytics and Application Insights )
Update May 2023: Things significantly improved since the time this was originally published and now Microsoft provides PowerShell to disable client IP address masking.
Update-AzApplicationInsights -Name <String> -ResourceGroupName <String> [-SubscriptionId <String>] -DisableIPMaskingOld text :
And Microsoft provides capability to accommodate this requirement with ease. In 1 minute you can disable IP masking and re-enable it back once the troubleshooting session is over.
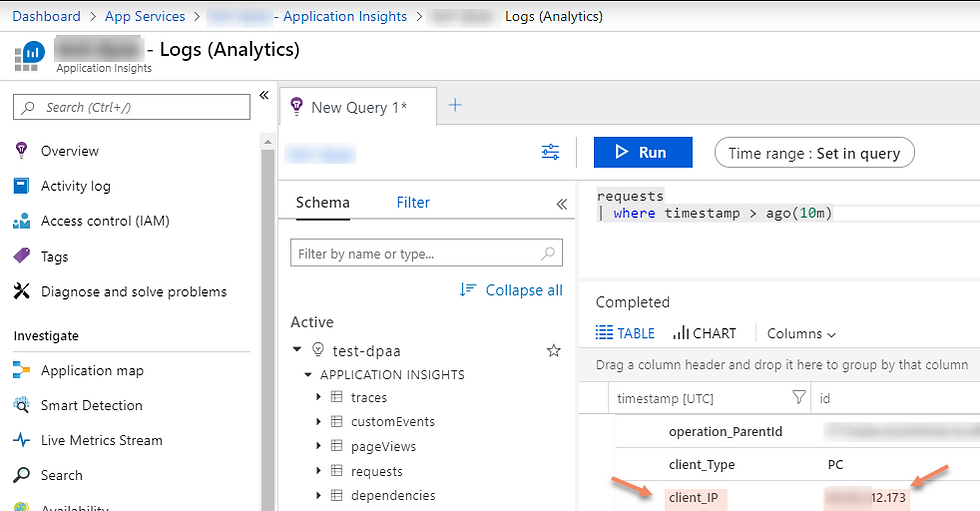
To start below we can see default Application Insights behavior (client IP information is masked)

While there are many ways to change this behavior probably the easiest is to go to Azure Resource Explorer , navigate to your Application Insights instance and update (or add) "DisableIpMasking" property like shown below.


Now we can observe that older records have client IP masked and new AI records contain actual client IP values.

Also in record detail we now can correlate client IP will all other information captured in AI. The settings affect web logs (AI "request" records) and application log("trace" records).
If later you need to find private data (including client IPs) stored in your Azure Log Analytics Microsoft also provides great AI query examples to look for private data.
Hope you find this useful and all the best on your cloud journey!



hey there, to help others as you helped me, i could write one more append to explain how to do it with arm templates as it was my way to accomplish the same behaviour when both methods failed.